Public key infrastructure (PKI)
Certificates & X509
Karol Babioch <karol@babioch.de>
NULL 911 - July 31, 2019
“How to delegate trust”
or: “Whom do you trust?”
Kazakhstan intercepts TLS traffic
In Kazakhstan, Internet connections via HTTPS are partly intercepted. According to various reports, providers in the central Asian country have asked their customers to install a special root certificate in their browsers that enables the interception. [...]
Source: Bulletproof TLS Newsletter #55
About me
- Open Source Enthusiast
- Engineering Infrastructure @ SUSE
- ❤ Crypto, authentication, IT security, ...
- karol@babioch.de
- 749A 65CD 479F 3215
- kbabioch
- Karol Babioch
- Karol Babioch
- Karol Babioch
- karolbabioch
- kbabioch
Agenda
- Introduction
- Overview & terminology
- Challenges & mitigations
- Q&A
Resources
Source: Bulletproof SSL and TLS by Ivan Ristić
Crypto 101
- Hash functions
- Digital signatures
(Cryptographic) hash functions
- (Fixed-size) digest (“hash value”) for any input
- Input → digest (easy)
- Digest → input (difficult)
- Unlikely for two messages to have same digest
(Cryptographic) hash functions
Source: Wikipedia
(Cryptographic) hash function
- ≠ encryption
- Also referred to as: One way hash functions
- Use cases: integrity, signatures, ...
- Examples: SHA1, SHA2 (256, 384, 512), SHA3, MD5
Digital signatures
- Requires one key pair (of sender)
- Digital signature = encrypted hash of message
- Recipient needs to know public key of sender
- Proves that sender has control over private key
Digital signatures
Source: Wikipedia
Introduction
Public key infrastructure
- Public key cryptography is only math
- Needs standards to be of value
Approaches for key distribution
- Trust-on-first-use (TOFU)
- Web of trust (OpenPGP)
- Public key infrastructure
Public key infrastructure
Roles, policies and procedures to
- create
- manage
- distribute
- use
- store
- revocate
public keys and certificates
X509
- Most prevalent PKI standard
- Usually PKI = X509
Used in many applications / protocols
- SSL/TLS
- IPsec
- VPNs
- S/MIME
- Smart cards
- nPA
Internet PKI
- Also Web PKI
- Used in browsers throughout the Internet
- CA/Browser Forum (CAB Forum)
- ≠ “private” PKIs
Other standards
- OpenPGP
- SSH CA (user & host keys)
Overview & terminology
Diagram of PKI
Source: Wikipedia
Certificate authority
- Entity issuing certificates
- Public key well known and distributed
Registration authority
- Entity validating identities
- Asks CA to issue and store certificates
Requesting certificate
- Subject requests certificate at RA
- RA validates identity ...
- ... and asks CA to issue certificate
Certificate signing request
- “Standardized” way to ask for certificate
- “Template” for certificate to be issued
- Signed by subject itself
Certificate
- Binding between public key and entity
Certificate fields
- Version
- Serial number
- Signature algorithm
- Issuer
- Validity
- Subject
- Public key
Certificate extensions
- Subject Alternative Name (SAN)
- Name constrains
- Basic constrains
- Key usage (KU)
- Extended key usage (EKU)
- Extended validation, ...
- ...
Anatomy of a certificate
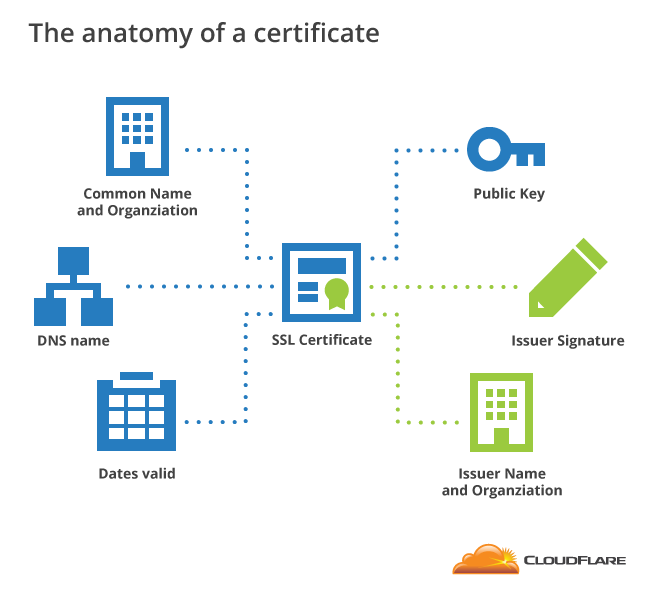
Source: Wikipedia
Certificate chains
- Certificate can be signed by intermediate CAs
- First/last CA is called Root CA
- Good practice (online vs. offline, etc.)
Certificate chains
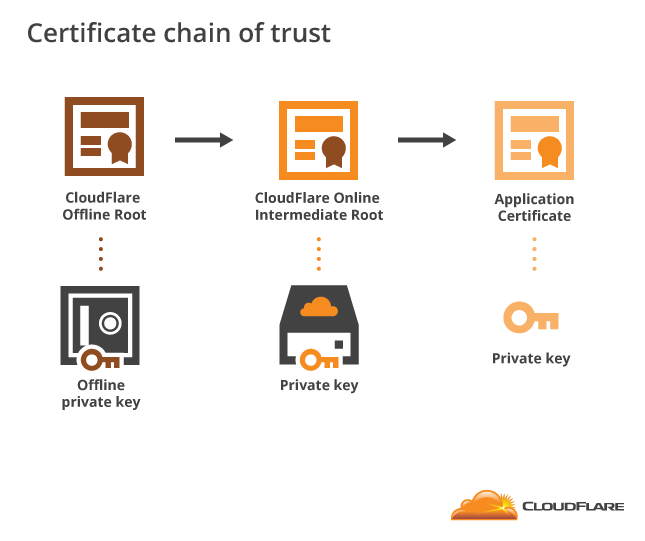
Source: Wikipedia
Certificate verification
- Subject (matching hostname, etc.)
- Expiry dates
- Constrains
- Key usage
- Revocation status
- ...
- Signed by trusted CA
- Do those checks for all intermediates
Trust stores
Trust stores
- CAs need to get their public keys into trust stores
- Trust stores are managed & distributed with OS vendors, browsers, etc.
- Rules & policies ...
Challenges & mitigations
Challenge
- Hundreds of CAs in trust stores
- Foo CA can issue wild card certificate for *.google.com
- Everyone trusting Foo CA will trust the certificate
- Foo CA can issue intermediate CA
Mitigations
- Constraints
- Pinning
- Certificate transparency
- CAA records
Constrains
- Certificates can have constrains
- Length of path
- Name (i.e. *.example.com)
- CA
Pinning
- Pin certificate(s) / key(s) / CA(s) in clients and applications
- Example: Chrome for Google assets
- HTTP Public key pinning (HPKP)
Certificate transparency
- All (good) CAs write to an append-only log
- Can be tracked, monitored and audited
- CAs will get in trouble in case of abuse ...
- ... but not technical enforcement
- Is publicly accessible
CAA records
- Special DNS records
- Describes which CA is allowed to issue certificates
- CAs will get in trouble in case of abuse ...
- ... but not technical enforcement
Certificate revocation
- Revocation is tricky / broken ...
CRL
- Original idea
- List of revoked certificates signed by CA
- Only certificates that are not expired yet
Issues with CRLs
- CRLs need to be re-issued regularly
- CRLs can become huge
OCSP
- Online Certificate Status Protocol
- Check during handshake whether certificate is valid
Problems with OCSP
- Availability
- Failing soft vs. failing hard
- Privacy
OCSP stapling
- Server regularly asks for OCSP status itself
- Attaches response to handshake
- Client checks OCSP status from server response
Problems with OCSP stapling
- Solves most of the previous issues
- Deployment rate ...
Short-lived certificates
- Only issue certificates for a short period of time
- Automate re-issuing and deploying certificates
- Example: Let's Encrypt
Let's Encrypt
Let's Encrypt
- Publicly trusted certificates for free
- Domain validated “only”
- Short-lived
- Automation via ACME (HTTP & DNS)
- Easy-to-use: Lot's of clients, scripts, etc.
Let's Encrypt statistics
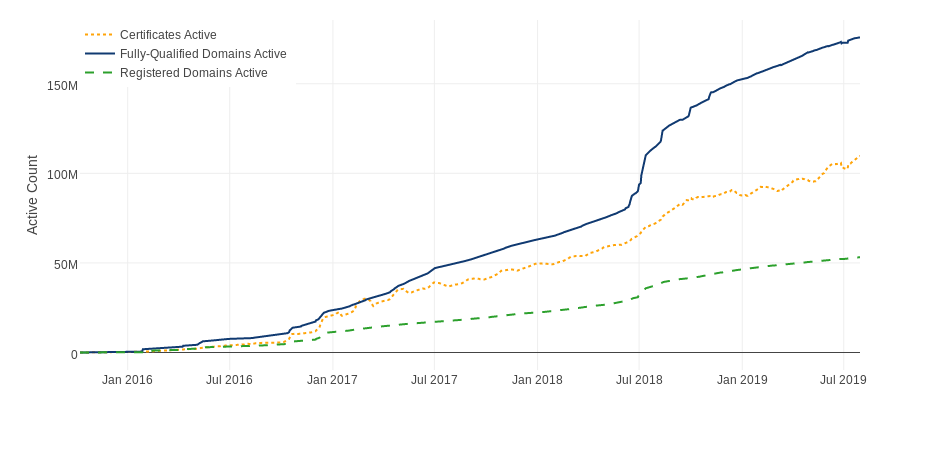
Source: Let's Encrypt
Let's Encrypt statistics
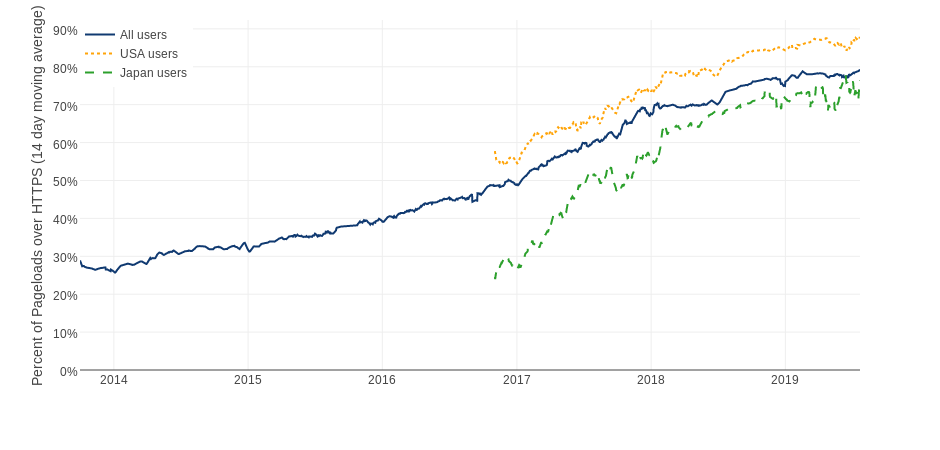
Source: Let's Encrypt
Formats & encoding
- ASN.1: Abstract description of complex data structures and objects
- BER: “Implementation” of ASN.1
- DER: Subset of BER used in X509
- PEM: ASCII encoding of DER using Base64
Formats & encoding
- DER / PEM can both encode different artifacts
- Certificates, keys, CSRs, CRLs, etc. pp.
DER / BER
- Binary data
- Uncomfortable to deal with
PEM
- ASCII data
- Comfortable to deal with (mostly used)
PKCS#12 / PFX
- Complex format (binary)
- Can store key + full certificate chain
PEM examples
-----BEGIN CERTIFICATE----- MIICMzCCAZygAwIBAgIJALiPnVsv [...] -----END CERTIFICATE-----
-----BEGIN RSA PRIVATE KEY----- izfrNTmQLnfsLzi2Wb9xPz2Qj9fQYGge [...] -----END RSA PRIVATE KEY-----
Formats & encoding
- File extensions are not helpful
- .crt, .cert, .cer, .key, .pem
- .pkcs12, .p12, .pfx
- .cer, .der
- Can be converted using tools (OpenSSL)
Tools for managing PKIs
- OpenSSL
- EJBCA
- XCA
- DogTag
- CFSSL
- Vault
- ...