Introduction to YubiKey
A small overview
Karol Babioch <karol@babioch.de>
openSUSE Conference 2019, May 24 2019
Some YubiKeys ...

Source: yubico.com
About me
- Open Source Enthusiast
- Working @ SUSE
- ❤ Crypto, authentication, IT security, ...
- YubiKey Maintainer (& Contributor)
- (open)SUSE
- Arch Linux
- karol@babioch.de
- 749A 65CD 479F 3215
- kbabioch
- Karol Babioch
- Karol Babioch
- Karol Babioch
- karolbabioch
- kbabioch
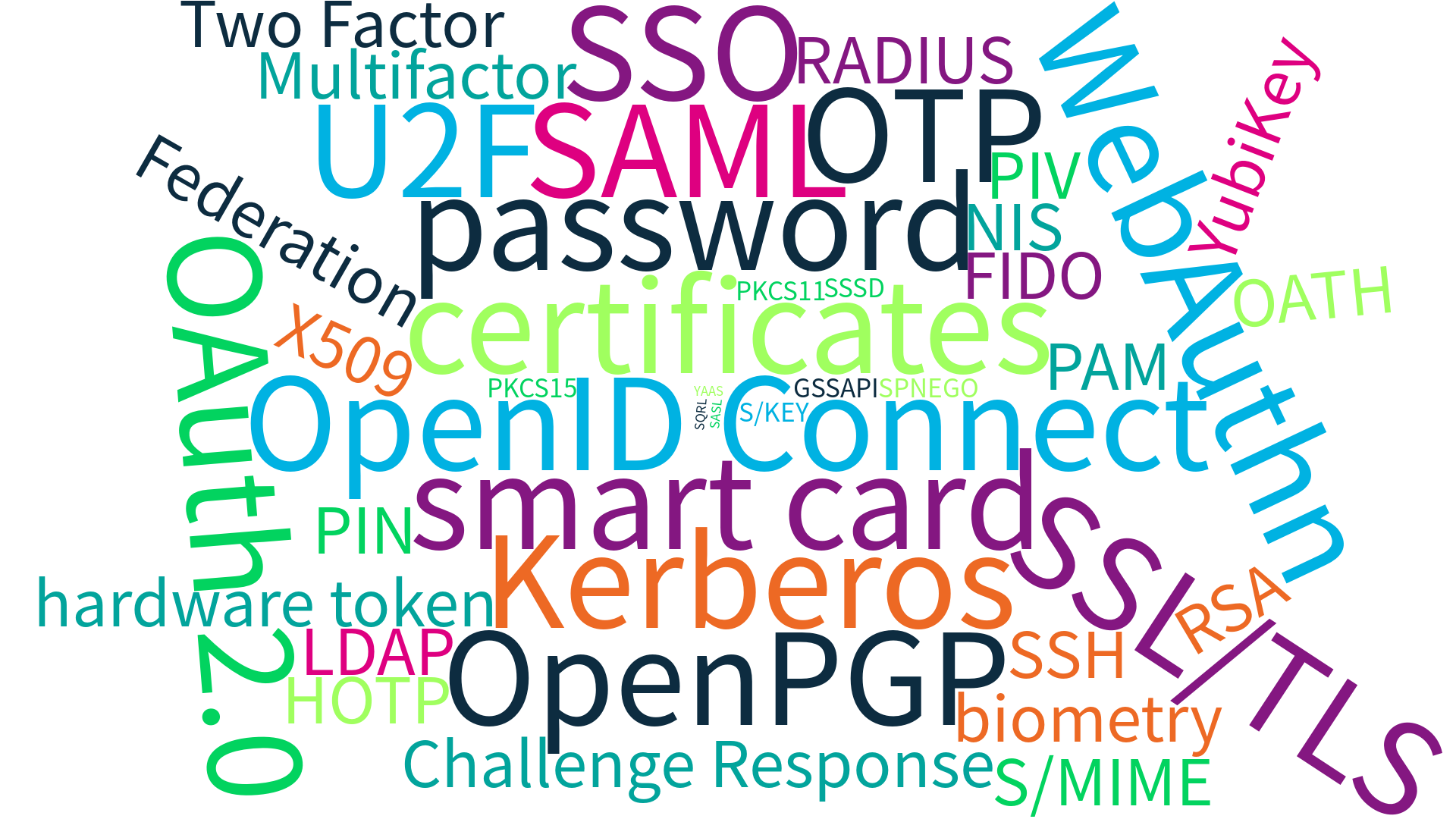
Agenda
- Authentication basics
- Problems with passwords
- Hardware tokens to the rescue
- One-time passwords (OTPs)
- U2F / WebAuthn / FIDO2
- OpenPGP smart card
- ‘Demo’ & Q&A
Resources
Authentication basics
Authentication is the act of confirming the truth of an attribute of a single piece of data claimed true by an entity.
[...]
authentication is the process of actually confirming that identity.
Source: Wikipedia
Context: User authentication
Who am I speaking with?
Authentication
- AuthN, A1, Au
- → Who am I?
Authorization
- AuthZ, AuthR, A2, Az
- → What am I allowed to do?
- Something you are
- Biometry, e.g. finger print, face, voice, iris, etc.
- Something you know
- Secrets, e.g. passwords, PINs, answers to questions, etc.
- Something you have
- (Physical) keys
- (Hardware) tokens (smart cards, certificates, YubiKeys, etc.)

Various combinations are feasible
→ Two-Factor-Authentication (2FA)
→ Multi-Factor-Authentication (MFA)

Passwords ...
... are great
- Easy to use
- Easy to implement
- Universal
- Recommendations & best practices (NIST, etc.)
... are challenging
- ‘Clueless’ users
- Weak passwords
- Password re-usage
- Phishing
- ...
- ‘Incompetent’ service providers
- ‘Breaches’
- Wrong practices (hashing, salting, etc.)
... difficult to handle
- Random passwords
oN9ee8$aihi%Wuho
- Hard to remember
- Password managers
- No fun to enter
... do not protect against
- Replay
- Phishing
- Man-in-the-Middle
... in reality
- Daily ‘breaches’
- Dumps with billions of passwords
- Wrong understanding (even from experts)
- Unlikely to change anytime soon
- Problematic since at least ~ 40 years
123456
&password
most used passwords (2017)
Hardware tokens


- Cryptography in secure environment
- Keys cannot be accessed
- No general-purpose CPU
- Only ‘limited’ feature-set
- Difficult to ‘hack’
- Difficult to clone
- (Some) protection from infiltrated hosts
- (Not updatable)
Let's use YubiKeys ...

Source: yubico.com
- Intuitive to use (touch, short vs. long)
- Similar to physical key
- Requires physical possession
- Different interfaces
- USB (HID) → keyboard
- NFC
- Bluetooth Low Energy (BLE)
- Several modes ...
- ... allowing for many different use-cases

Source: yubico.com
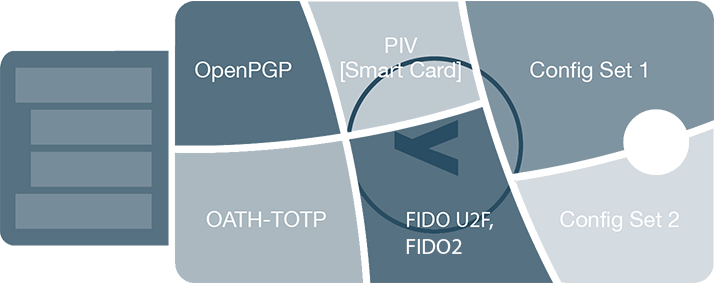
Source: yubico.com
One-time passwords (OTP)
Basic idea
- Short lived passwords ...
- ... used as additional factor (2-FA)
Delivery channels
- Hardware tokens (RSA, Gemalto, etc.)
- (Smartphone) applications
- Smart card (TAN, etc.)
- Text message (SMS)
- ...
- YubiKey (several modes)
Yubico OTP
- Original mode that started Yubico (~ 2007)
- Idea: YubiKey acts as keyboard
- YubiKey enters OTP into field
- Service providers verify OTP
Example output (modhex)
cccjgjgkhcbbirdrfdnlnghhfgrtnnlgedjlftrbdeut cccjgjgkhcbbgefdkbbditfjrlniggevfhenublfnrev cccjgjgkhcbbcvchfkfhiiuunbtnvgihdfiktncvlhck
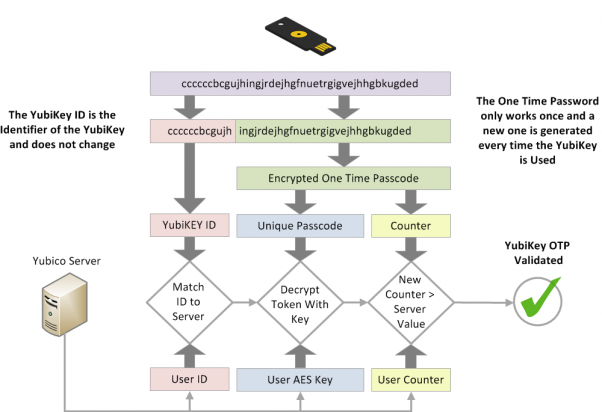
Source: yubico.com
More information
- Comes pre-configured
- Based on shared secret
- Involves third party
- Hosting for yourself is possible (*)
- Scales well (for users)
Usage in openSUSE
- Works out of the box
yubikey-manager
&yubikey-manager-qt
for basic configurationpam_yubico
for local authentication (PAM)
Drawbacks
- Limited number of service providers
- Requires network connectivity
OATH (HOTP & TOTP)
- Standards for one-time passwords
- OATH != OAuth
- TOTP: Time-based
- HOTP: Event-based
- Usually 6-digit codes
- YubiKey emulates keyboard
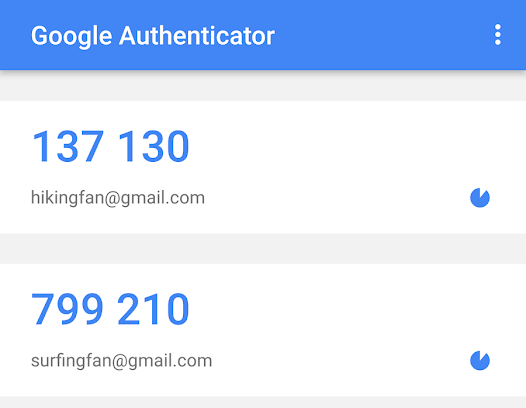
More information
- Based on shared secret
- No network connectivity required
- Requires initial configuration
- Only additional factor
- No third parties involved
Usage in openSUSE
- Supported out of the box, but ...
- ... requires individual configuration
yubikey-manager
&yubikey-manager-qt
for configurationpam_yubico
and/orpam_oath
for local authentication
Drawbacks
- Initial setup (‘advanced’)
- Scales badly (for users)
Problems with OTPs ...
- OTPs increase security ...
- ... and have a cool touch to it, ...
- but
- don't solve a lot of problems!
Problems with OTPs ...
- Inconvenient
- Unsafe recovery processes
- Active attacks (Man-in-the-Middle, session hijacking, etc.)
- Based on shared secrets
- Scales badly!
U2F / FIDO2 / WebAuthn
Overview
- Standards for public key cryptography
- User authentication in the web
- Vision: Successor to passwords
- Easier to use than OTPs
- Driven by FIDO Alliance & W3C
- Idea: (Hardware-based) Authenticator + support in browser
History
- U2F was originally developed by Google, Yubico & NXP (2012)
- Donated to FIDO Alliance → FIDO U2F (2013)
Evolution
- FIDO2 = Advancement & ‘modularization’ of U2F
- Server-client communication → WebAuthn
- Client-authenticator communication → CTAP
Quasi-synonym
We are going to use U2F / FIDO2 / WebAuthn mostly synonymously, ...
... although this is technically not correct!
- Server → Relying Party (RP)
- Generates and delivers JavaScript
- Browser → Client
- Executes JavaScript
- Proxy between relying party and authenticator
- Authenticator
- Abstract model
- Hardware token, e.g.. YubiKey
- Software, e.g. operating system
Ceremonies
- Registration
- Authentication
- (Account recovery)
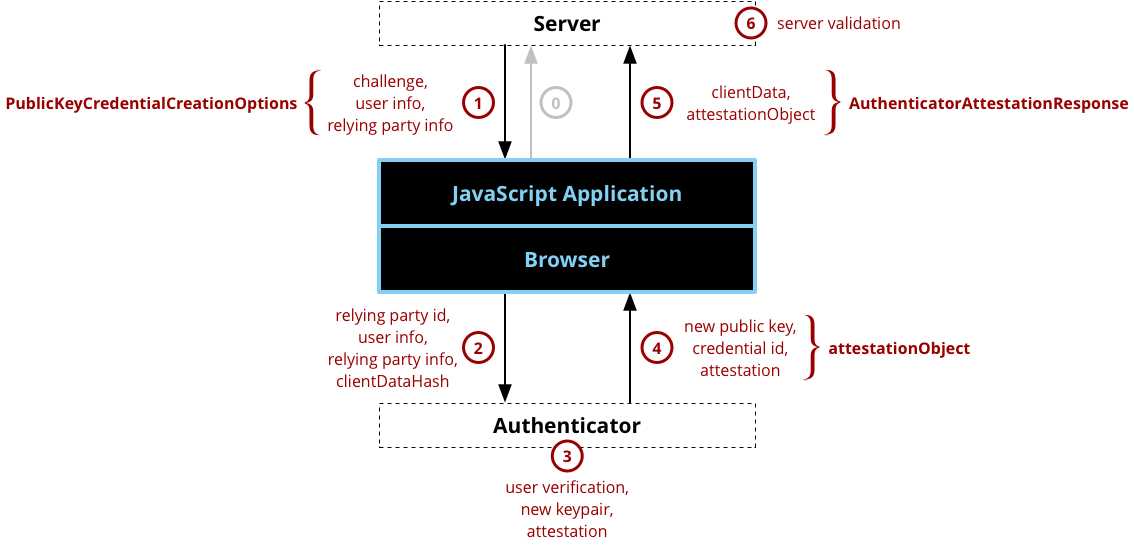
Source: Mozilla
User experience
- Surf the web
- ‘Touch the button’ of your YubiKey
Usage in openSUSE
- Works out of the box with modern browsers
- Firefox:
security.webauth.u2f
→true
(about:config) yubikey-manager
&yubikey-manager-qt
for basic configuration
Browser support
- Google Chrome 67
- Mozilla Firefox 60
- Microsoft Edge (build 17723)
- Apple Safari (preview)
- Opera
Innovative concept
- Individual key pair for each service
- Random bit patterns can be used as key
- Keys are generated on-the-fly ...
- ... deterministically based on
- URL of website
- device-specific secret
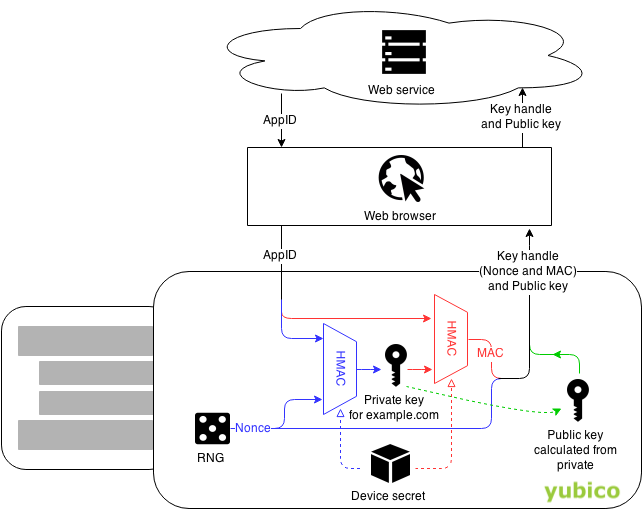
Source: Yubico
Advantages
- Scales well for users with many services
- Built-in phishing protection
- No storage of key material necessary
- No traceability between different services
- Service provider only gets useless information
OpenPGP smartcard
OpenPGP
- Mostly known from email encryption ...
- ... and package signing
- Can also be used for SSH authentication ...
- ... using the GPG as SSH agent
Usage in openSUSE
- Supported out of the box with
gpg2
- Requires some setup (environment variables, etc.)
- Usage:
ssh root@...
Advantages
- Keys are stored in hardware
- Smart card protected by PIN
- Will be blocked after three failed attempts
Other use-cases
- Personal Identity and Verification Card (PIV)
- Challenge-Response (password managers, etc.)
- Static passwords
- Bluetooth / NFC (mobile)
More details
- Workshop tomorrow @ 15:00
- developers.yubico.com
- yubico.com
- webauthn.io
- Talk about U2F, FIDO2 & WebAuthn @ Chemnitzer Linux Tage 2019 (German)
Summary
- Passwords by itself are insecure
- YubiKeys are easy to use ...
- ... and increase security
- Many different options and use cases
- You should get one, ...
- ... and start using it
Demonstration
- OTPs
- U2F / WebAuthn
- OpenPGP smart card